本文仅限技术研究与讨论,严禁用于非法用途,否则产生的一切后果自行承担。
小维
漏洞描述
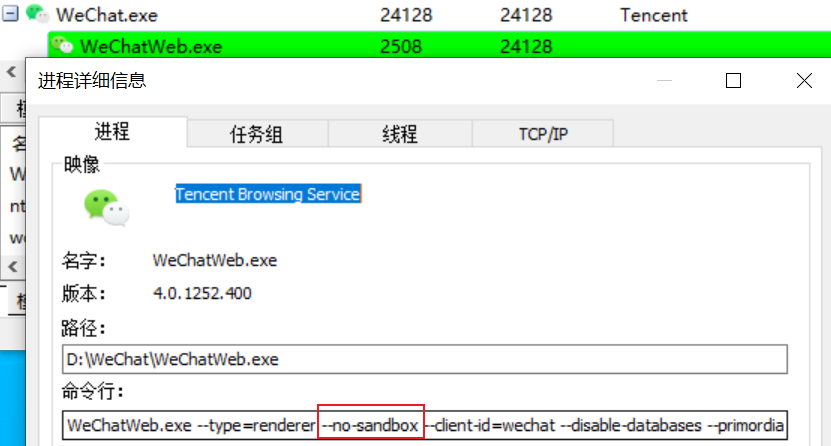
该漏洞是Google V8引擎历史漏洞的衍生关联漏洞。微信客户端(Windows版本)使用V8引擎解析JavaScript代码,并关闭了沙盒模式(–no-sandbox参数)。攻击者利用上述漏洞,构造恶意钓鱼链接并通过微信发送,在引诱受害者使用微信客户端(Windows版)点击钓鱼链接后,可获取远程主机的控制权限,实现远程代码执行攻击。
影响范围
微信PC客户端(Windows)< 3.2.1.141 (注:亲测较低版本可能不存在)
漏洞复现
环境介绍
1 | 操作系统:Windows 10 |
微信打开链接时会调用WeChatWeb.exe进程,默认使用–no-sandbox,构造好对应的POC即可实现攻击。
exp.html
1 | <script> |
效果
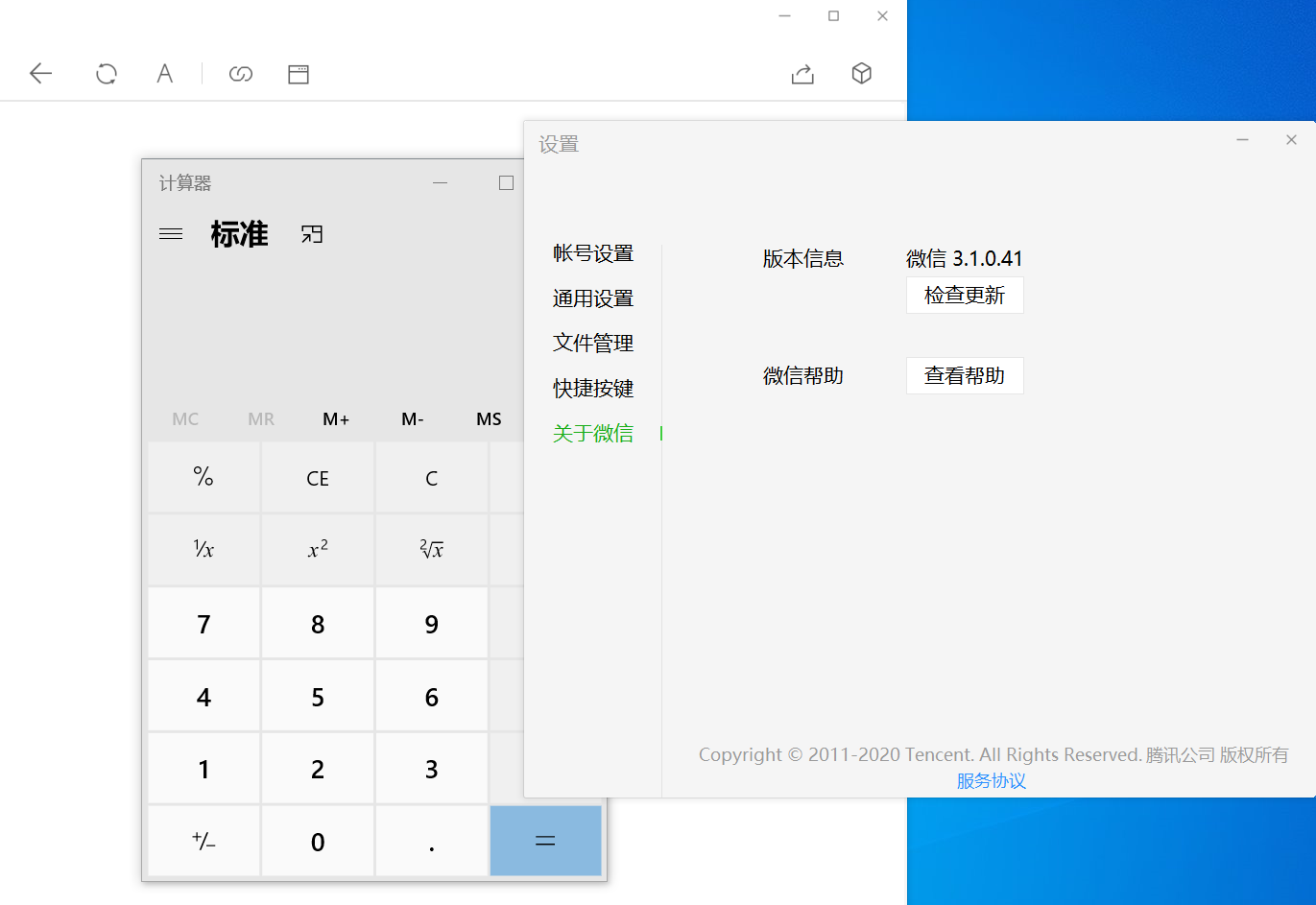
将恶意的exp.html部署在HTTP服务上,使用微信内置浏览器打开部署好的链接,成功弹出计算器。
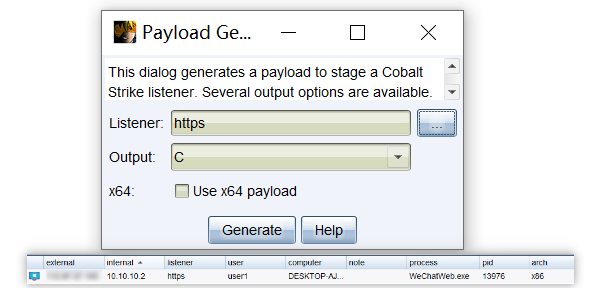
将exp.html中的计算器Shellcode替换成CS生成好的Shellcode(32位),实现CS上线。
处置建议
微信新版本修复该漏洞,建议用户立即将微信 (Windows版)更新至最新版本。